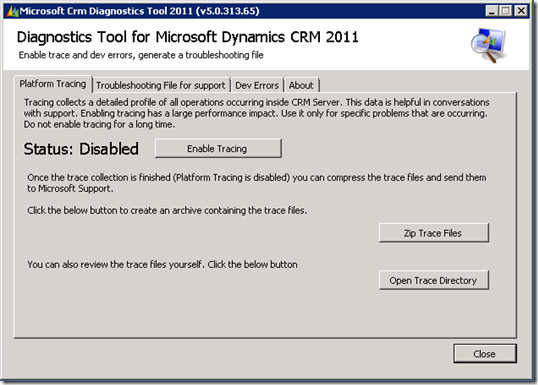
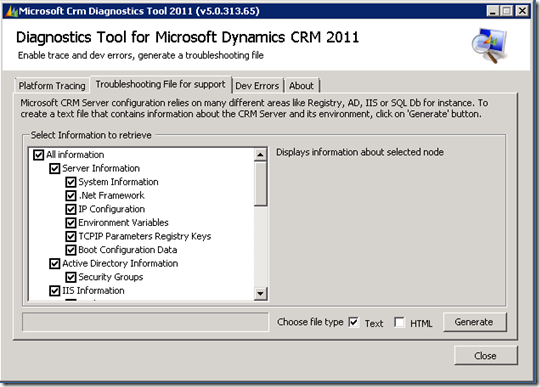
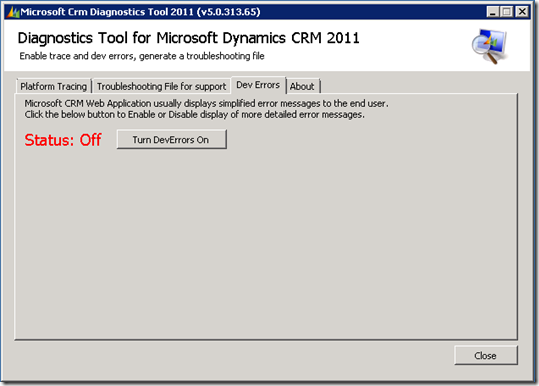
This post is going to answer questions regarding ISA 2006/ FAG and CRM 2011 Claims and IFD.
For this post we chose to let ISA handle the SSL Certificates as this is the common scenario for ISA deployments although other methods can be used.
We chose to focus this blog on letting CRM handle the authentication while letting ISA handle the SSL session. The main reason for using IFD despite ISA’s ability to provide forms based authentication was that the Microsoft Dynamics CRM Clients for Outlook would run into authentication problems if prompted with an ISA login. In order to get CRM running with IFD a good starting point is to study the IFD guide called How to configure an Internet-Facing Deployment for Microsoft Dynamics CRM 4.0 it can be downloaded from the Microsoft Download Center. The deployment guide will allow you to better understand the CRM 4 IFD concepts before you create any publishing rules on ISA Server.
Adjusting the Dynamics CRM 2011 Server for External Publishing
To deploy this scenario the following topology was used:

Figure 1 – Topology using CRM 2011 IFD/ Claims with ISA Server 2006.
ISA Publishing will be the same for CRM 2011 but you have to publish 4 rules.
org.contoso.com (will be used over https port 444)
sts1.contoso.com (will be used over https port 443)
auth.contoso.com (will be used over https port 444)
dev.contoso.com (will be used over https port 444)
======================================================================================
This is content from http://www.dynamics-crm-2011.de | Dieser Beitrag ist von http://www.dynamics-crm-2011.de
Themen rund um CRM 2011 onpremise, Dynamics CRM 2011 Online, Dynamics CRM 2011 mit IFD und Claims.
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
For this post we chose to let ISA handle the SSL Certificates as this is the common scenario for ISA deployments although other methods can be used.
We chose to focus this blog on letting CRM handle the authentication while letting ISA handle the SSL session. The main reason for using IFD despite ISA’s ability to provide forms based authentication was that the Microsoft Dynamics CRM Clients for Outlook would run into authentication problems if prompted with an ISA login. In order to get CRM running with IFD a good starting point is to study the IFD guide called How to configure an Internet-Facing Deployment for Microsoft Dynamics CRM 4.0 it can be downloaded from the Microsoft Download Center. The deployment guide will allow you to better understand the CRM 4 IFD concepts before you create any publishing rules on ISA Server.
Adjusting the Dynamics CRM 2011 Server for External Publishing
To deploy this scenario the following topology was used:

Figure 1 – Topology using CRM 2011 IFD/ Claims with ISA Server 2006.
ISA Publishing will be the same for CRM 2011 but you have to publish 4 rules.
org.contoso.com (will be used over https port 444)
sts1.contoso.com (will be used over https port 443)
auth.contoso.com (will be used over https port 444)
dev.contoso.com (will be used over https port 444)
======================================================================================
This is content from http://www.dynamics-crm-2011.de | Dieser Beitrag ist von http://www.dynamics-crm-2011.de
Themen rund um CRM 2011 onpremise, Dynamics CRM 2011 Online, Dynamics CRM 2011 mit IFD und Claims.
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++


 05:26
05:26
 Dynamics Consulting München
Dynamics Consulting München





 Posted in:
Posted in: